Firewall,What is a Firewall?,Defined,Explained,Explored What is Firewall?,Fire Wall,How Firewall Technology Works?,Firewall – Computer Network Security System
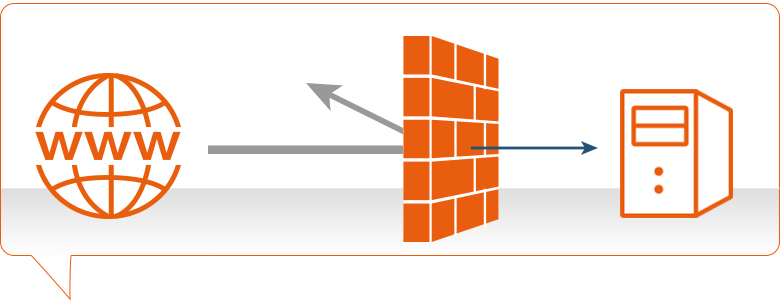
A firewall is a network security device located between your internal network and the wider Internet. A firewall monitors incoming and outgoing network traffic – blocking or allowing it based on a set of configurable rules.
Firewalls are a fundamental piece of security and typically form the first line of defence on a network. Acting as a filter against bad connections from the outside world.
A firewall works by comparing the data sent into or out of the network against a list of rules. Based on the results of the rule checking, the firewall will then either block or allow the connection.
How does a firewall work?
Firewalls work by inspecting data packets (small chunks of data) against an internal list of rules. Here are some of the more common ones:
- IP addresses – filter out traffic from suspicious IPs
- Domain names – block traffic from known malicious domains
- Ports – deny traffic trying to enter through a certain port
- Contents – block data packets containing certain keywords
A firewall scans the contents of the packet and then determines whether to let it through based on the rules in place. On a typical network setup, all connections to the Internet flow through the firewall. Meaning it inspects all inbound or outgoing packets.
How does firewall inspection work?
The process of inspection involves comparing a packet’s contents against the firewall’s set of rules. Depending on if the rule is setup as a blacklist or whitelist, it will react differently to a match.
- A blacklist rule will block any packets which match the criteria.
- A whitelist rule will block any packets which don’t match the criteria.
A firewall’s rules are highly configurable. Meaning you can make the packet inspection process unique to your security setup. Here are some examples of how you could use custom firewall rules:
- Creating a whitelist for your own company IP. Preventing any outsiders from accessing what’s behind the firewall.
- Making a blacklist for the IP of a known malicious file server. Stopping it from distributing malware onto your network.
- Creating a whitelist for certain domain extensions (.com, .co.uk .edu e.t.c.) on outgoing traffic. Blocking staff from accessing potentially dangerous sites.
Why are firewalls important?
Firewalls are often compared to a lock on the door to your network. But it might be more accurate to say that a firewall is the door.
Without a firewall in place, any connection can flow freely in or out of your network. Including connections from known malicious sources. This means you could experience unauthorised access to networked files. Leading to a data breach, malware infection or worse.
You need a firewall to filter out the bulk of malicious connections. And there’s a lot of malicious connections. One study found that within 52 seconds of being online, servers were being probed by hackers. With an average rate of 757 connection attempts per hour.
Are firewalls hardware or software?
Firewalls can be either a hardware appliance or a piece of software which runs on a machine. So, the answer is both.
Not helpful, I know.
But the main difference between the two is this:
- Software firewalls tend to protect the individual machine it’s installed upon, typically a laptop or PC
- Hardware firewalls usually protect many machines or an entire network.
What types of firewall are there?
Circuit-level
Circuit level firewalls are a type of firewall that monitors transmission control protocol (TCP) handshaking. It ensures that the communication between packets is legitimate and not malicious.
Stateful inspection
A firewall with stateful inspection considers the state of current connections when filtering packets. This means that the firewall can block the packet in one case but allowed in another. Depending on the current state of the connection.
Unified threat management (UTM)
Whilst technically not a type of firewall, UTM is instead an advanced security appliance which combines the security functions of many different security appliances. One of these being a firewall. We have an article explaining everything you need to know about UTM if you wish to learn more.
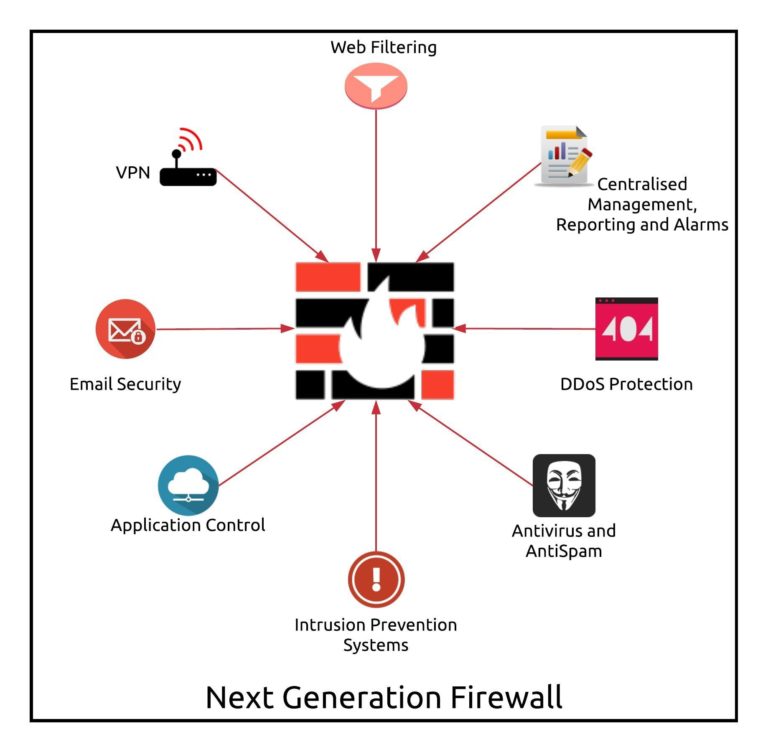
What is a next-generation firewall?
A next-generation firewall (NGFW) contains all the normal defences that a traditional firewall has and more. The most common additions are intrusion prevention software and application control. But certain vendors have other bonus security features. NGFWs are also capable of deep packet inspection which enables more robust filters.
Intrusion prevention software monitors network activity to detect and stop vulnerability exploits from occurring. This is usually done by monitoring for breaches against the network policies in place.
Application control software sets up a hard filter for programs that can send or receive data over the Internet. This can either be done by blacklist (blocks any programs in the filter) or by whitelist (blocks any programs not in the filter).
What is deep packet inspection?
Deep Packet Inspection (DPI) is a type of packet inspection which analyses the full contents of a data packet. Instead of only information in a packet’s header (where it is coming from and going to).
This enables DPI to filter out malicious packets, such as viruses and trojans, with better accuracy. As rather than only looking at the sender and destination, the packet’s contents can be used in filters as well.
This allows DPI to uncover a broader range of security threats because it will discover packets with a malicious payload but an innocuous header.
Where did the name firewall come from?
A final piece of trivia: the name firewall originated from the real-world application of fire partitions used in buildings. These would be walls that were implemented into a building to act as a barrier to stop fire spreading from one room to another.
The similarity between a fire spreading through a building and a computer virus spreading through a network prompted the same name to be adopted for the network device.
[WPSM_AC id=13860]
Sales Number : +91 95 8290 7788
Support Number : +91 94 8585 7788
Sales Email : sales@itmonteur.net
Support Email : support@itmonteur.net
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India


































